ObserveIT ITM 內部威脅偵測及阻絕之應用
威脅偵測範例項目 |
ObserveIT ITM 應用 |
| 異常時段登入系統 |
|
| 瀏覽內部機敏資訊平台或外部高風險網站 |
|
| 未經授權複製機敏資料至外接儲存裝置或上傳至外部雲端硬碟 |
|
| 寄送機敏資料至外部信箱或與競業進行聯繫 |
|
| 未經授權之安裝/解除程式、帳號建立、異常執行序、提權等 |
|
| 存取機敏資料夾或共享磁區、編輯文件與圖片 |
|
| 應用程式、機敏資料夾、內/外部網站之機敏字串搜尋 |
|
| 使用LINE、Skype或Messenger等社交應用程式 |
|
ObserveIT ITM 資料外洩預測之應用
DLP範例項目 |
ObserveIT ITM應用 – 偵測、告警、阻絕及視覺化側錄 |
| 上傳檔案至外部雲端平台及應用程式 |
|
| 於內部機敏資訊平台上傳/下載檔案 |
|
| 可卸除式儲存裝置使用監控 |
|
| Email資料外洩防禦及監控 |
|
| 檔案列印、複製/貼上 |
|
| Key-Logging告警/偵測/控管 |
|
| 複製/貼上機敏文字 |
|
| 存取未授權資料夾及檔案 |
|
| 執行惡意/駭客工具 |
|
| 執行圖像隱碼術工具 |
|
| 於Linux/Unix系統執行檔案傳送指令 |
|
| 使用P2P工具 |
|
ObserveIT ITM 資安事件調查與回應之應用
資安事件調查需求 |
ObserveIT ITM 應用 |
| 即時的高可視性 |
|
| 加密及不可否認性 |
|
| Google-like 搜尋 |
|
| 注重隱私、去識別化 |
|
ObserveIT ITM 遠距/分散/居家/辦公之應用
遠距/分散/居家辦公之需求 |
ObserveIT ITM 應用 |
| 維持妥適的資安防護措施並符合各類規範 |
|
| 防範機密資料不外洩 | |
| 阻絕使用者異常行為 | |
| 資安事件時,快速而有效地調查與回應 | |
| 管理並維持員工的生產力 |
ObserveIT ITM 法令遵循之應用
ISO27001 控制項目 (部份) |
ObserveIT ITM應用 |
|
|
SWIFT國際組織CSP控制項目 (部份) |
|
|
符合國際規範之加密機制,確保資料之安全及不可否認性

- 所有Metadata及視覺化記錄除了採用Microsoft SQL Server本身之加密機制,再以AES Like 安全加密方式存放,確保證據無法竄改,具備證據之不可否認性。
- 提供專屬加密播放器回播加密格式側錄資料,確保回播過程之安全性。
- 資料傳輸過程中採SSL或TLS加密機制,資料傳輸時無法盜取或竄改。
- 所有 Agent 均符合 FIPS 國際安全規範,端點資料安全無虞。
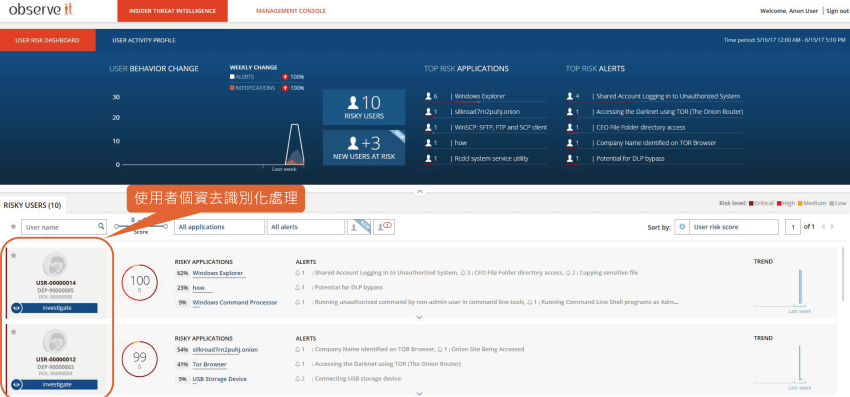
隱私及去個資識別化機制,符合國際個資隱私之規範遵循

- 個資去識別化,確保個人資料不外露。
- 可自訂管理者瀏覽項目之權限,避免管理或稽核人員獲取權限以外之個資。
- 回播操作過程時可額外設定回播密碼。
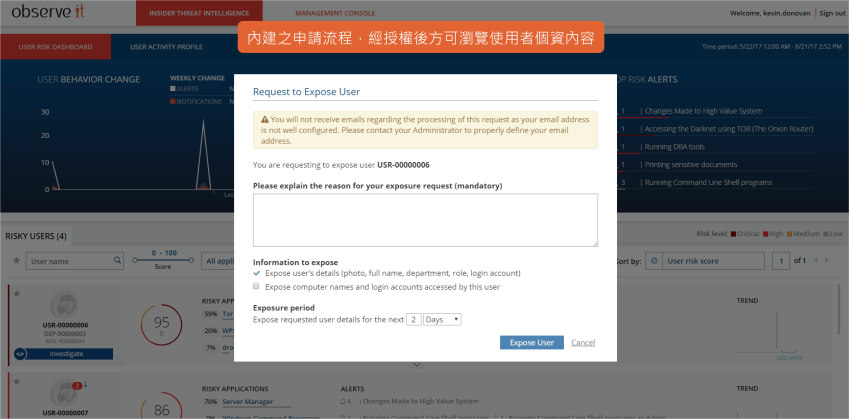
- 內建申請流程,經授權後方可進一步檢視資料內容。
- 符合 PCI, HIPAA, FISMA, GDPR & CCPA 國際遵循規範對於個資及隱私之要求。
ObserveIT ITM - A People-Centric Approach to Managing Insider Threats

以「人」為中心的內部威脅管理是企業組織最有效的資安防禦策略,藉由影片所介紹之Always-On監控方式,實際案例介紹 ObserveIT ITM 即時掌握使用者活動內容且兼顧隱私又符合法令遵循,達成及時回應的資安防禦目標。
Live Demo:A People-Centric Approach to Insider Threat Management
影片介紹如何運用 ObserveIT ITM 達成以下資安管理目標:
- 有效減少事故調查時間 60~90%。
- 運用使用者活動與檔案活動軌跡之關聯性,提前偵測內部威脅有關的資安事故。
- 如何與組織內部關係人有效溝通並衡量資安風險。